


Phishing has been around for years. Internet phishing began when people started sending instant messages and emails to AOL customers posing as AOL employees. These messages requested users to verify their account or billing information. The users would fall for this and unknowingly handover their passwords. The “phishers’ would then be able to get access to the user’s AOL accounts.
Not much has changed since then in the way phishing is done. In fact attacks have only gotten more sophisticated and easy to conduct. The phishers have many more channels through which they can deliver messages - Emails, SMSes, Instant Messengers, Social Media etc. The impact of a successful phishing attack has also increased many fold due to our dependence on digital and internet services.
As a phisher, setting up a phishing attack is easy. Let’s take the example of Email Phishing which is by far the most common form of phishing. All you need are the following:
A well designed phishing email with a malicious link
A mail server to send the email
A similar looking domain to the original one (say g00gle(dot)com)
A landing page that shows a fake page (say a fake login page)
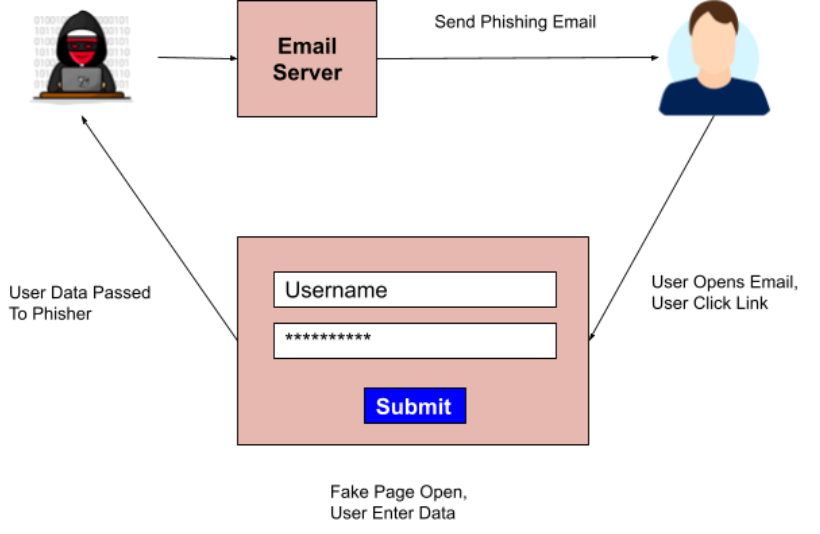
The phisher can design a good phishing email using his creative abilities.
The phisher can make use of any Mail Service Providers that allows you to send a specific number of emails / day for free. He can also set up his own email server for more control.
A similar looking domain can be cheaply bought from any of the registrars such as GoDaddy, Google Domains or Name Cheap.
A landing page can then be created by the phisher that will look exactly like the original page.
There are free and open source tools that do most of the things mentioned above.
Any person with a bit of technical knowledge can conduct a phishing attack with ease. And that is why it is very dangerous. With very little investment in time and money, a phisher can get hold of your sensitive information such as username, passwords, credit card numbers, personal information etc. These can then be used to perform malicious activities leading to a huge financial gain for the phisher and loss to the phished person or organization.
It is thus important to be safe from phishing attacks. But how can you be safe? There are two ways:
Use of technology
Awareness
There are various technical solutions available to ensure that people don’t get phished. To start with, most email service providers can detect a phishing email and ensure that it does not reach your inbox. For organizations that have implemented their own email infrastructure, there are services that help in filtering out bad emails. There is also continuous monitoring and detection of bad mail servers and domains. Once identified as malicious, they are added to blacklists. This ensures that phishing emails do not reach your Inbox. These are the ones that end up in your Spam / Junk folder.
However, there can be instances when phishers are able to bypass these checks. For such cases, Google has come up with a service called Google Safe Browsing. It is basically a list of domains and URLs that are considered as dangerous. Whenever a person accesses such a domain or URL, a bright red warning is displayed informing the user that the site is unsafe.
However, in our experience, we have detected that it takes at least one day for a phishing URL to be included in the Google Safe Browsing blacklist. That is a sufficient amount of time for a phisher.
Technical solutions are available and are effective to a large extent and should definitely be utilized. But there is a significant chance that phishing emails will still reach your employee’s inbox. Hence, it is necessary to make employees aware of phishing.
It is very important for employees to be aware of phishing. Primarily:
What is phishing?
What are the dangers of phishing?
How to identify a phishing email?
What to do if a phishing email is received?
There are different ways in which you can teach employees about phishing. You can:
Conduct classroom/online people based training
Conduct online video based training
Send periodic mailers etc.
All of these are useful methods and should be implemented.
But, is training alone enough? Training is akin to patching. Patching is important and all systems should be updated to the latest version. You may have implemented a process to ensure that all systems are periodically patched. But does that stop you from doing a Vulnerability Assessment of your systems? NO! We periodically perform Vulnerability Assessments to check if there are any vulnerabilities in the system. If any vulnerabilities are found, they are patched. A Vulnerability Assessment helps you identify weaknesses that exist in your system even after performing periodic patching.
So how do you find if people are vulnerable to phishing attacks even after conducting periodic training?
By conducting regular Phishing Simulation Exercises.
A phishing simulation mimics real phishing attacks by sending “malicious” emails to employees. Ofcourse, they are not really malicious! It won’t install ransomwares or collect your credentials for nefarious purposes. It will however let us know which employees can and cannot detect a phishing email. Typically, a phishing simulation will give us the following information about the employees:
Did they open the email?
Did they click on the “malicious” link in the email?
Did they submit sensitive information (such as password)?
Did they report about phishing to relevant people (e.g. InfoSec / IT team)?
These are useful information that can be used in various ways. The first thing is to basically re-train the employees who failed. Secondly, after performing phishing simulation over time, you will have enough data to determine the most vulnerable employees. These may be employees who repeatedly fall for phishing even after repeated training. You can then consider implementing additional safeguards for these employees to ensure that the impact of a successful real phishing attack is minimized.
But, how do you conduct a phishing simulation exercise?
There are basically two ways:
Do It Yourself (DIY) using Open Source Tools
Get it done from a cyber security company - either as a service or a product
If you are tight on budget, you can do it yourself. There are various Open Source tools fit for purpose. But, in our opinion, GoPhish is one among the best. It is easy to set up and use. You can design emails and clone landing pages. You can then run the campaign and see the result in a good dashboard.
There is however one problem. You need to have a mail server that will send emails. Ideally, you should be able to make use of any commercial Mail Service Provider such as Google and Office 365. But, these providers block you from sending emails in bulk the moment they detect that you are sending way too many emails than normal. They will also block emails that look spammy or phishy.
The next option is to send emails by using a transactional email service provider such as SendInBlue, SendGrid, Mailgun etc. You will be able to send emails up to a particular limit every hour / day depending on the provider. However, this is also not an ideal solution as they too will block emails the moment they detect that you are sending spammy or phishy emails.
The primary reason email service providers block you from sending phishing emails is because they need to maintain their IP reputation. Every time you send phishing emails using the email service provider, their IP reputation takes a hit. This will in turn impact their service as legitimate emails of their other customers will also end up in the Spam / Junk. Hence, they have a strict policy against sending such kinds of emails.
So, the only practical solution is to set up your own Mail Server. Open Source Solutions such as iRedMail and Modoboa can help you set up one. Note that you need a server that has Port 25 open so that it can function as an SMTP server. Most ISPs and Cloud Service Providers block Port 25 to ensure that not many bad email servers are up and running in their infrastructure. You would need to request your service provider to open Port 25 so that you can run the mail server. Some service providers, such as Digital Ocean, do not open Port 25 at all. Also, before running the simulation, it is recommended to whitelist your mail server’s IP address in your receiving mail service such as Gmail or Office365 to ensure that mail from your mail server reaches your employee’s inbox.
Once you have GoPhish and mail server setup you can run the phishing simulation.
If you don’t want the hassle of doing it yourself, the best option is to take the service of a cyber security company experienced in doing phishing simulation. They will set up everything, run the campaign and give you the result. You can also ask for a dedicated phishing training (for employees who fail) to be included in the service.
There are also products that you can subscribe to. Most of them provide the capability to do phishing simulation as well as training. Some of the well known products include:
KnowBe4
LUCY Security
Cofense
Boxphish
INFOSEC
Hoxhunt and many many more
Shameless plug here!!! :-)
We, Risk Quotient, with years of experience in conducting phishing simulation exercises have developed our own phishing simulation & training tool called 4Phish. We have our own dedicated mail server using which emails are sent. The tool was built to ensure that our phishing simulation service is top notch. With our own tools and experts, we can now do customized phishing simulations which were earlier not possible for us to do.
We provide 4Phish as a service as well as a product.
As a service, we agree with you on the number of phishing simulations to be done in the year. We work closely with you to design the phishing campaign and we execute the program for you.
As a product, you get access to the tool, our email server and a set of email templates and landing pages. You can then run as many campaigns as you like. We will provide our support wherever you require. All this for a much lower investment than most of the similar tools available in the market.
If you are interested in 4PHISH, get in touch:
Email - sales@rqsolutions.com
Office - +91 9137572379